Essential Network Scanning Tools Enhance Security and Performance
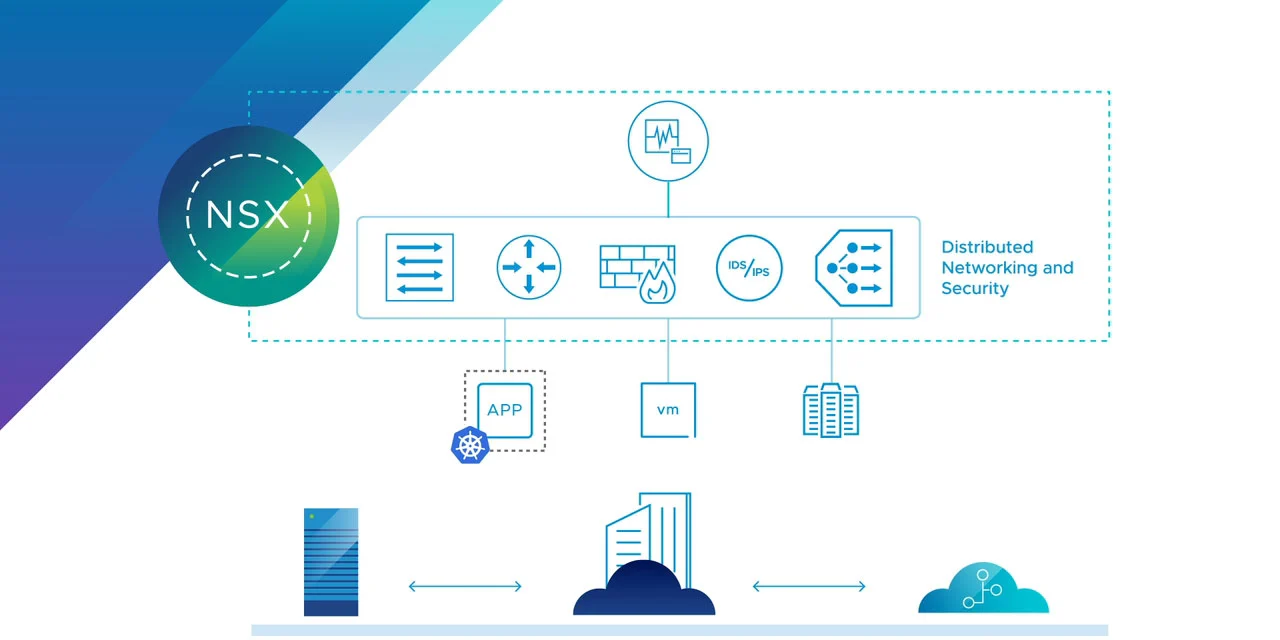
Securing network infrastructures has become paramount in an era of digital transformations reshaping business landscapes. Network scanning tools are essential for IT administrators, cybersecurity professionals, and ethical hackers to assess and monitor network security. These tools help in identifying active devices, open ports, vulnerabilities, and potential threats within a network. By scanning IP addresses, detecting unauthorized access points, and analyzing network traffic, they play a crucial role in preventing cyberattacks and ensuring a secure network infrastructure.
Whether used for penetration testing, compliance checks, or routine network maintenance, these tools provide valuable insights into network performance and security weaknesses. With the growing complexity of digital environments, choosing the right network scanning tool is vital for organizations to protect their data and maintain a robust security posture.
What Are Network Scanning Tools?
Network scanning tools are software applications used to detect and analyze devices, services, and vulnerabilities within a network. They help IT professionals and cybersecurity experts identify active hosts, open ports, and potential security risks. These tools are essential for network security, troubleshooting, and performance optimization. By scanning for weaknesses, unauthorized access points, and misconfigurations, they aid in preventing cyber threats. Popular tools like Nmap, Wireshark, and Nessus provide deep insights into network health, making them crucial for maintaining secure and efficient networks.
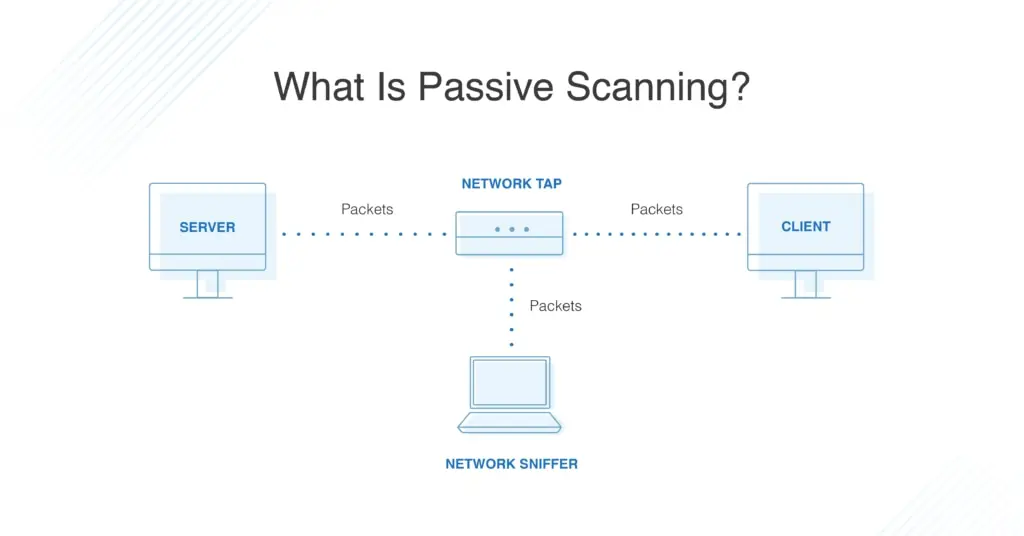
Why is network scanning important?
Network scanning is crucial for maintaining security, performance, and efficiency in any IT infrastructure. It helps identify active devices, open ports, vulnerabilities, and unauthorized access points, allowing organizations to detect potential security threats before they can be exploited by attackers. By regularly scanning networks, IT professionals can uncover misconfigurations, outdated software, and weak security protocols that may expose systems to cyber threats.
Additionally, network scanning plays a key role in compliance with security regulations and standards, ensuring that businesses meet cybersecurity requirements. It also helps in network optimization by monitoring traffic patterns, detecting bottlenecks, and improving overall network performance. Whether used for penetration testing, threat detection, or routine maintenance, network scanning is an essential practice to enhance security, prevent breaches, and ensure a stable IT environment.
The Role of Network Scanning Tools
Network scanning tools play a vital role in ensuring cybersecurity, network efficiency, and overall IT infrastructure management. These tools help identify devices, active hosts, open ports, and vulnerabilities within a network, allowing administrators to assess security risks and take proactive measures. By scanning for misconfigurations, weak passwords, outdated software, and unauthorized access points, these tools help prevent potential cyber threats such as hacking, malware, and data breaches.
In addition to security, network scanning tools contribute to performance optimization by monitoring network traffic, detecting bottlenecks, and identifying underutilized resources. They also assist in compliance with security regulations by ensuring that networks adhere to industry standards and best practices. Whether used for penetration testing, threat detection, or routine maintenance, network scanning tools are essential for maintaining a secure and efficient IT environment.
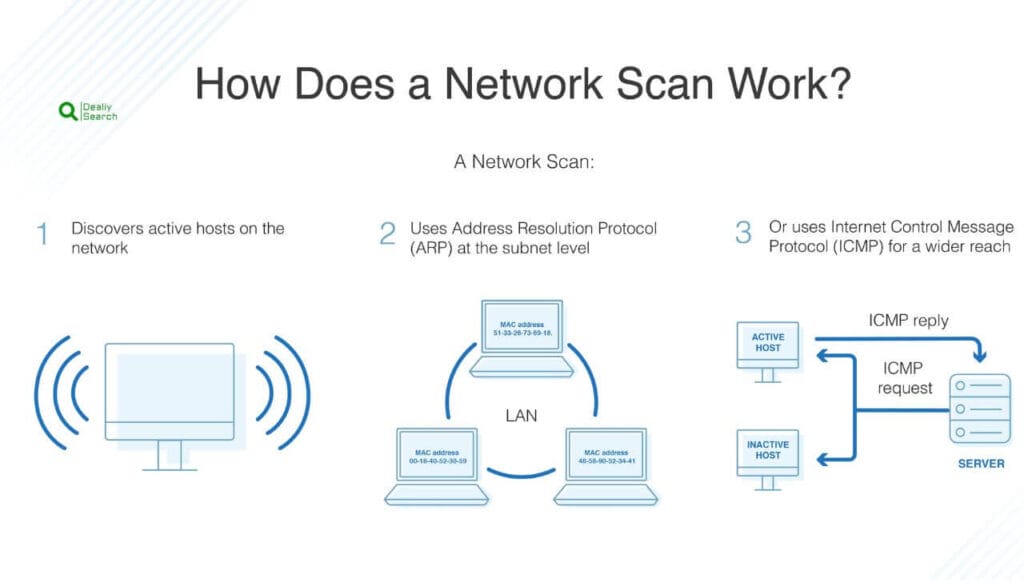
How does network scanning work?
Network scanning works by actively probing a network to identify connected devices, open ports, and security vulnerabilities. It begins by sending requests to IP addresses within a network and analyzing the responses to determine which devices are active. These tools use different scanning techniques, such as ping sweeps to detect live hosts, port scanning to check for open and closed ports, and vulnerability scanning to identify weaknesses that attackers could exploit.
Advanced network scanning tools can also detect running services, operating systems, and firewall rules to provide a comprehensive view of network security. Ethical hackers and IT professionals use these scans to assess potential threats, ensure proper configurations, and strengthen security measures. By regularly scanning the network, organizations can prevent unauthorized access, detect anomalies, and maintain a secure IT environment.
How to Choose the Right Network Scanning Tool
Choosing the right network scanning tool depends on your specific security and network management needs. First, consider the purpose of the tool whether you need it for vulnerability assessment, penetration testing, or routine network monitoring. Different tools specialize in various functions, such as Nmap for port scanning, Wireshark for packet analysis, and Nessus for vulnerability scanning. Next, evaluate the features offered by the tool, including automation, real-time monitoring, reporting capabilities, and integration with other security systems.
Ensure it supports your network size and infrastructure, as some tools work better for small businesses, while others cater to large enterprises. Additionally, check for ease of use and cost-effectiveness. Some tools are open-source and free, while others require subscriptions. Finally, consider security compliance and vendor support to ensure smooth operation and timely updates.
Best Network Scanning Tools
Nmap (Network Mapper): One of the most popular open-source network scanning tools, Nmap is used for port scanning, network discovery, and security auditing. It helps detect active hosts, services, and vulnerabilities.
Wireshark: A powerful packet analyzer that captures and inspects network traffic in real time. It is widely used for troubleshooting and security analysis.
Nessus: A leading vulnerability scanner that detects security flaws, misconfigurations, and compliance issues in networks and systems.
Angry IP Scanner: A fast and lightweight IP scanner that quickly identifies active devices on a network, making it useful for small businesses and IT professionals.
Advanced IP Scanner: A user-friendly tool that provides network device detection, remote access, and monitoring features.
OpenVAS (Open Vulnerability Assessment Scanner): A comprehensive vulnerability scanning tool that helps organizations detect security risks and maintain compliance.
Zmap: A high-speed network scanner designed for large-scale scanning of internet-wide networks.
SolarWinds Network Performance Monitor: A commercial tool with advanced network scanning, monitoring, and performance analysis features for enterprises.
Each of these tools serves different purposes, from basic network discovery to advanced security analysis, helping IT professionals maintain a secure and efficient network.
Benefits of network scanning tools
Network scanning tools enhance security, detect threats, optimize performance, and ensure compliance by identifying vulnerabilities and monitoring network activity.
- Enhanced Security: Identifies vulnerabilities, misconfigurations, and unauthorized access points to prevent cyber threats.
- Network Visibility: Provides a clear view of all connected devices, open ports, and running services for better management.
- Threat Detection: Helps detect malware, suspicious activity, and potential security breaches in real time.
- Performance Optimization: Identifies network bottlenecks, ensuring efficient bandwidth usage and improved performance.
- Regulatory Compliance: Assists organizations in meeting security standards such as GDPR, PCI-DSS, and ISO 27001.
- Preventive Maintenance: Helps IT teams proactively address security gaps before they become major issues.
- Automation & Efficiency: Automates scanning processes, reducing manual workload and improving network security posture.
Frequently Asked Question
Here are some frequently asked question about network scanning tools:
What are network scanning tools used for?
Network scanning tools are used to identify devices, open ports, vulnerabilities, and security risks within a network. They help IT professionals monitor, troubleshoot, and secure network infrastructure.
Are network scanning tools legal to use?
Yes, network scanning tools are legal when used for authorized security assessments, penetration testing, and IT management. However, unauthorized scanning of external networks may violate cybersecurity laws.
What is the difference between port scanning and vulnerability scanning?
Port scanning detects open and closed ports on a network, while vulnerability scanning identifies security weaknesses and misconfigurations in devices and applications.
Can network scanning tools detect malware?
Some network scanning tools can detect suspicious activities, unusual traffic, or vulnerabilities that could indicate malware, but they are not a replacement for antivirus software.
Which network scanning tool is best for beginners?
Angry IP Scanner and Advanced IP Scanner are user-friendly for beginners, while Nmap provides more advanced scanning features with a learning curve.
How often should I scan my network?
Regular scanning is recommended—weekly or monthly for businesses, and more frequently for high-security environments. Automated scanning can help maintain continuous security monitoring.
Do free network scanning tools provide reliable results?
Yes, many free tools like Nmap and Wireshark offer powerful scanning capabilities, but paid tools like Nessus or SolarWinds provide advanced features and dedicated support.
Conclusion
Network scanning tools are essential for ensuring the security, efficiency, and reliability of modern IT infrastructures. They help identify vulnerabilities, detect threats, optimize network performance, and ensure compliance with security standards. Whether used for penetration testing, routine monitoring, or troubleshooting, these tools provide valuable insights into network activity and potential risks.
Choosing the right tool depends on your specific needs, from basic IP scanning to advanced vulnerability assessments. Regular network scanning is a proactive approach to safeguarding data, preventing cyberattacks, and maintaining a secure and well-functioning IT environment.