DDoS Defense Tactics: Proactive Measures for Safeguarding Your Network Infrastructure
In the rapidly evolving digital landscape, Distributed Denial of Service (DDoS) attacks represent one of the most pervasive threats to online stability. Managing DDoS attacks efficiently ensures business continuity, protects user data, and maintains service availability. This article delves into the nature of DDoS threats and outlines robust strategies for mitigating their impact.
Table of Contents
Understanding DDoS Attacks
What is a DDoS Attack?
A Distributed Denial of Service (DDoS) attack is a malicious attempt to disrupt the regular traffic of a targeted server, service, or network by overwhelming the target or its surrounding infrastructure with a flood of Internet traffic. DDoS attacks achieve their effectiveness by utilizing multiple compromised computer systems as sources of attack traffic. These systems can include computers and other networked resources, such as IoT devices.
The primary approach is to overload the target with so much traffic that it cannot respond to legitimate queries, effectively taking it offline. This can have significant consequences for businesses, including loss of revenue, erosion of customer trust, and, in some cases, long-term damage to a brand.
DDoS attacks can be categorized into several types, including but not limited to:
- Volume-based attacks include ICMP floods, UDP floods, and other spoofed-packet floods. The goal is to saturate the bandwidth of the attacked site, and magnitude is measured in bits per second (Bps).
- Protocol Attacks: These include SYN floods, fragmented packet attacks, and Ping of Death, which aim to consume actual server resources or those of intermediate communication equipment, like firewalls and load balancers. They are measured in packets per second (Pps).
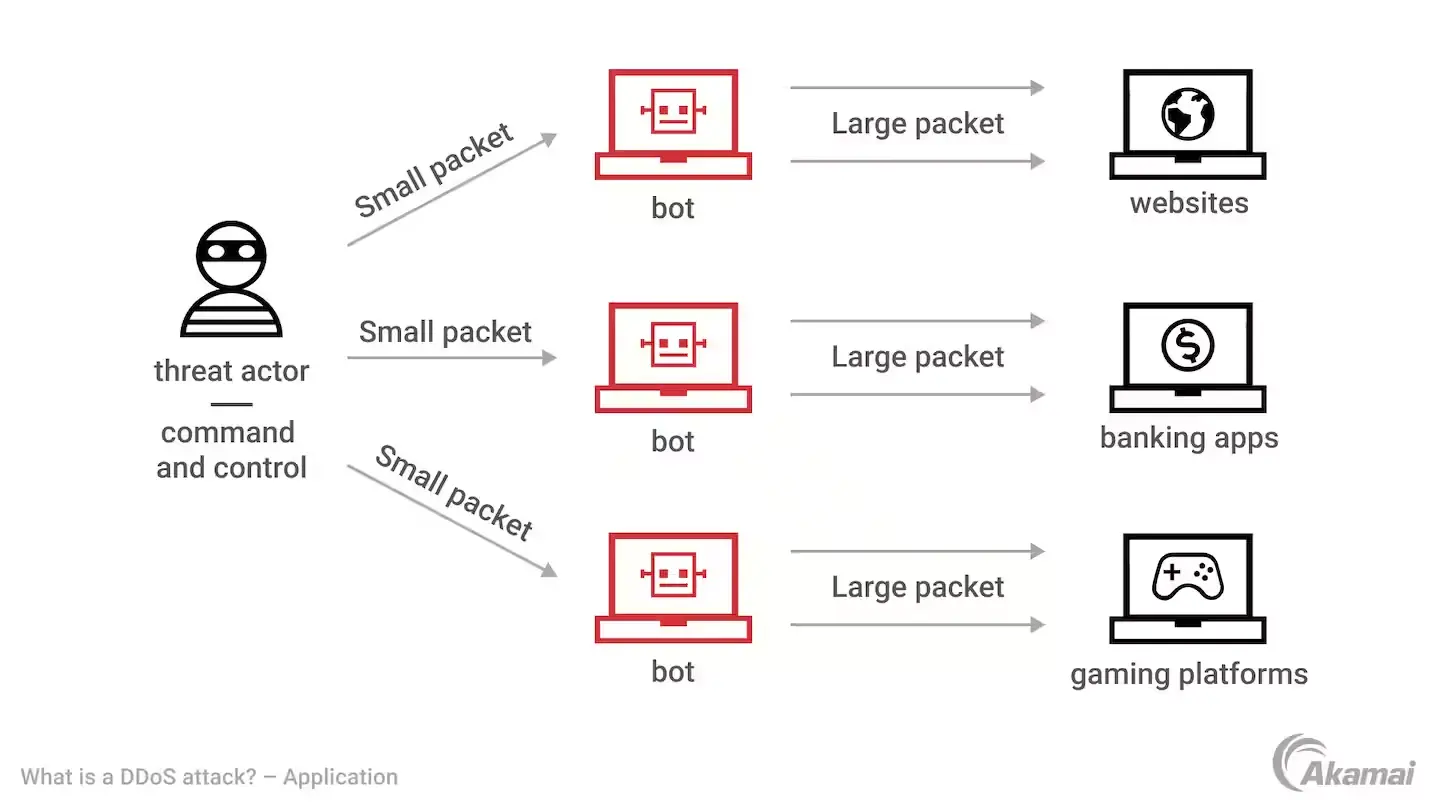
- Application Layer Attacks: These are more sophisticated and involve overwhelming a specific aspect of an application or service. They are measured in requests per second (rps). Examples include targeting the web server layer, the database layer, or direct application command logic.
DDoS attackers typically recruit botnets by spreading malicious software through emails, websites, and social media. Once infected, these machines can be controlled remotely to perform attacks without their owners’ knowledge.
DDoS attacks are increasingly common and are used not only to target businesses but also to carry out personal vendettas, make political statements, or distract from other cybercrimes. Defending against such attacks typically involves various strategies, including, but not limited to, rate limiting, web application firewalls, and anti-DDoS solutions provided by ISPs and cloud service providers.
Common Types of DDoS Attacks
Application-layer attacks are particularly insidious because they mimic legitimate requests and target specific elements of a web application. This can make them harder to detect and defend against than other types of DDoS attacks. They operate by exploiting the functionality of an application, overwhelming it with requests to the point where it can no longer handle legitimate traffic. These attacks are measured in requests per second (Rps).
Common examples of application-layer attacks include:
- HTTP Floods: This type of attack sends what appears to be legitimate HTTP requests but in overwhelming numbers that can cripple a web service.
- Slowloris: Designed to hold as many connections to the target web server open for as long as possible, Slowloris sends partial requests, periodically adding headers to keep the connections from timing out. This exhausts server resources as it tries to keep these fake connections alive.
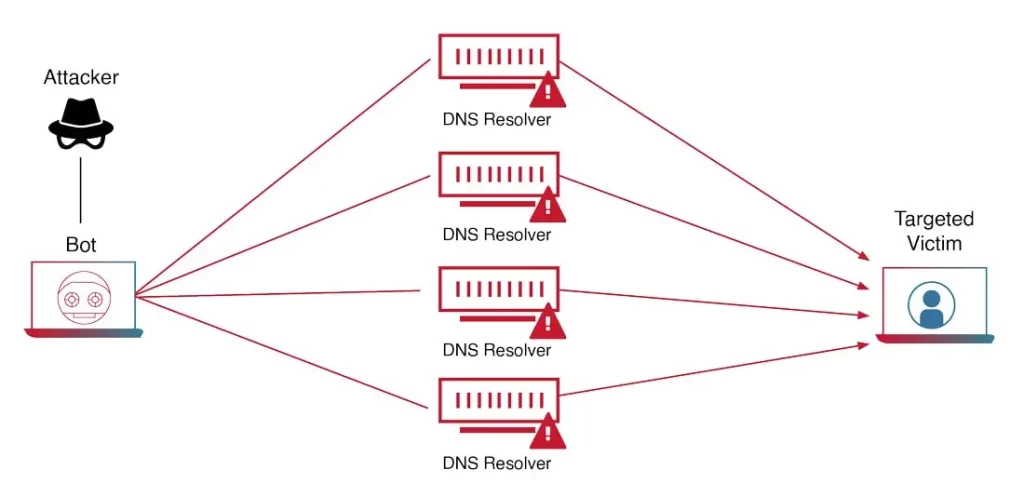
- DNS Query Flood: This attack bombards a domain’s DNS servers with rapid and numerous queries that mimic real search requests. The server is so busy handling the flood that legitimate queries can no longer be processed.
- Zero-day DDoS: These attacks exploit previously unknown vulnerabilities, making them extremely difficult to defend against until the vulnerability is identified and a patch or workaround is developed.
Defensive measures against application-layer attacks include:
- Rate Limiting: Setting up thresholds for the number of requests from a single IP address or session, helping to prevent overloading by rejecting or delaying requests once the threshold is crossed.
- Web Application Firewalls (WAFs): These can inspect incoming traffic and block requests that appear to be part of an attack.
- Scalability Solutions: Implementing scalable cloud infrastructure that can adjust resources as needed to handle traffic surges can effectively mitigate the effects of DDoS attacks.
- Behavioral Analysis: By monitoring how users typically interact with the application, anomalous, potentially malicious behavior can be flagged and filtered out.
When combined with traditional network security measures, these defensive strategies provide a robust defense against the increasingly sophisticated nature of application-layer attacks.
Strategic Framework for Managing DDoS Attacks
Effective management of DDoS threats involves preparation, response, and recovery. Here’s how organizations can fortify their defenses against such disruptions:
.
- Infrastructure Design and Optimization
- Minimize Attack Surface: To reduce exposure to potential attacks, utilize firewalls, load balancers, and content delivery networks (CDNs).
- Enhanced Network Architecture: Incorporate redundancy and high-capacity bandwidth to absorb and mitigate volumetric attacks.
- Proactive Monitoring and Detection
- Regular Traffic Analysis: Monitor network traffic to identify unusual spikes or patterns indicative of a DDoS attempt.
- Implement Anomaly Detection Systems: Use advanced software tools to detect and alert real-time anomalies.
- Robust Response Strategy
- Develop a DDoS Response Plan: Document specific actions to mitigate an attack, including notification procedures and escalation paths.
- Engage a DDoS Mitigation Service: Partner with specialized services offering additional support and advanced technologies during an attack.
Advanced Mitigation Techniques
Managing DDoS attacks becomes more manageable with the right tools and strategies in place. Here are some advanced techniques:
Infrastructure Layer Mitigation
- Rate Limiting: Control the traffic rate allowed through network touchpoints to prevent overload.
- Web Application Firewall (WAF): Deploy WAFs to block harmful traffic and filter out unwanted requests.
Application Layer Mitigation
- Multi-Factor Authentication (MFA): Protect application access and reduce the risk of exploitation.
- Passive Caching: Use caching mechanisms to serve requests without accessing the actual server, thus reducing load under spike conditions.
FAQs ( How do you manage and mitigate DDoS attacks effectively?)
FAQs: How do you manage and mitigate DDoS attacks effectively?
1. What is a DDoS attack, and why is it essential to mitigate?
- A Distributed Denial of Service (DDoS) attack is a malicious attempt to disrupt the regular traffic of a targeted server, service, or network by overwhelming it with a flood of internet traffic.
- Mitigating DDoS attacks is essential to maintaining online services’ availability, integrity, and performance, preventing financial losses, and protecting the organization’s reputation.
2. What are the common types of DDoS attacks?
- Volumetric Attacks: Flood the target with a high traffic volume, often using botnets or amplification techniques.
- Protocol Attacks: Exploit vulnerabilities in network protocols to consume server resources or disrupt communication between devices.
- Application Layer Attacks: These attacks target specific applications or services with malicious requests, aiming to exhaust server resources or cause application failures.
3. How can organizations prepare for DDoS attacks before they occur?
- Implement DDoS mitigation solutions: Deploy dedicated hardware appliances, cloud-based DDoS protection services, or hybrid solutions to detect and mitigate attacks in real time.
- Develop an incident response plan: Establish protocols for identifying, responding to, and mitigating DDoS attacks, including roles and responsibilities, communication procedures, and escalation paths.
- Conduct regular DDoS drills: Simulate DDoS attack scenarios to test the effectiveness of mitigation measures, refine response procedures, and train personnel.
4. What proactive measures can be taken to mitigate DDoS attacks during an incident?
- Traffic filtering: Block malicious traffic at the network perimeter using firewalls, intrusion prevention systems (IPS), or dedicated DDoS mitigation appliances.
- Rate limiting: Implement rate-limiting policies to restrict the number of requests or connections from individual IP addresses, preventing excessive consumption of server resources.
- Anycast routing: Distribute incoming traffic across multiple geographically dispersed servers or data centers using Anycast routing to absorb and mitigate DDoS attacks.
5. How can organizations identify and differentiate between legitimate and malicious traffic during a DDoS attack?
- Traffic analysis: Monitor network traffic patterns and anomalies using network monitoring tools, intrusion detection systems (IDS), or flow analysis solutions to identify DDoS attack traffic.
- Behavioural analysis: Utilize anomaly detection techniques to identify deviations from normal user behaviour, such as sudden spikes in traffic volume or unusual access patterns.
6. What role do content delivery networks (CDNs) play in mitigating DDoS attacks?
- CDNs help mitigate DDoS attacks by distributing content across multiple edge servers and data centers. They also reduce the impact of volumetric attacks by absorbing and filtering malicious traffic closer to the source.
- CDNs also provide caching and load-balancing services, improving the availability and performance of web applications during DDoS attacks.
7. How can organizations collaborate with internet service providers (ISPs) to mitigate DDoS attacks?
- Establish relationships with ISPs and upstream network providers to implement traffic filtering and rate-limiting measures upstream, closer to the source of the attack.
- Coordinate with ISPs to redirect traffic through scrubbing centers or blackhole routes to mitigate DDoS attacks targeting specific IP addresses or network segments.
8. What post-incident steps should organizations take to mitigate the impact of DDoS attacks and prevent future occurrences?
- Conduct a post-mortem analysis to evaluate the effectiveness of DDoS mitigation measures, identify weaknesses or gaps in security controls, and implement remediation actions.
- Update incident response plans and security policies based on lessons from DDoS attack incidents, incorporating new mitigation techniques and best practices.
- Monitor and review network security posture, infrastructure vulnerabilities, and threat intelligence to proactively identify and mitigate potential DDoS attack vectors.
Conclusion
Managing DDoS attacks requires vigilance, advanced planning, and the implementation of robust security measures. By understanding the nature of these threats and deploying a comprehensive defensive strategy, organizations can protect themselves from the significant disruptions caused by DDoS attacks. Remember, the key to managing DDoS attacks effectively lies in solid defensive tactics and a proactive, prepared approach to cyber threats.
Ensuring continuous monitoring, employing cutting-edge mitigation services, and maintaining an updated response plan are paramount in managing DDoS attacks in today’s digital world. Stay protected, stay vigilant.