Securing Your Digital Infrastructure: Network Scanning Tools Every Administrator Needs
Securing network infrastructures has become paramount in an era of digital transformations reshaping business landscapes. Network scanning tools have emerged as essential in safeguarding digital environments, facilitating robust network management, and preempting cyber vulnerabilities. This blog post explores these tools’ importance, functionalities, and the top network scanning solutions for 2024.
Table of Contents
Understanding Network Scanning Tools
What is Network Scanning?
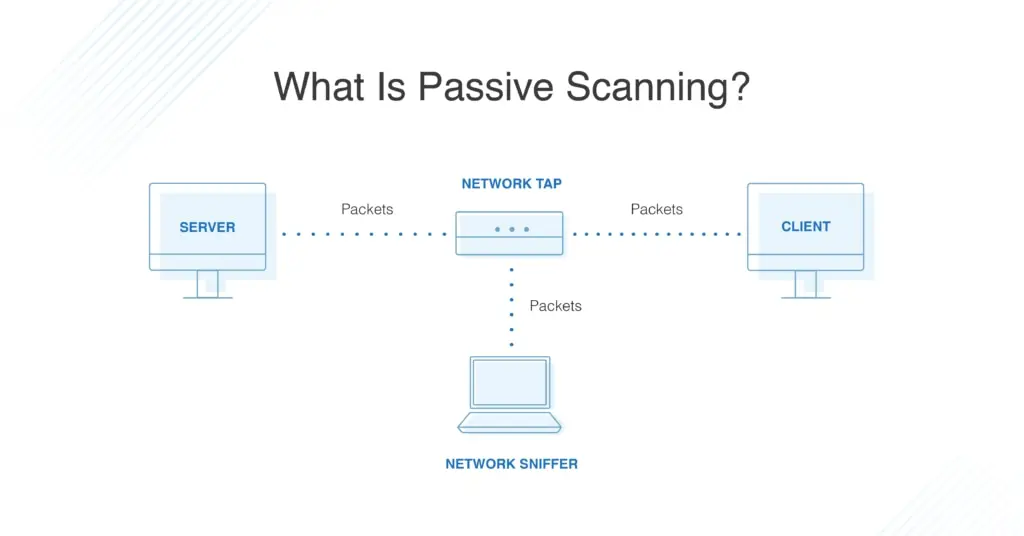
Network scanning is a critical process involving examining and managing network devices. It helps identify all the devices connected to a network, including routers, switches, and servers and assesses their vulnerability to security threats. This activity is fundamental to network management and security, allowing administrators to understand the network’s structure, detect unauthorized devices, and ensure that each component operates securely within the intended framework.
Beyond simple identification, network scanning also includes analyzing the services and ports that are open on devices. This involves checking for unused or insecure ports that could serve as entry points for attackers. Network scanners can detect issues such as outdated software, missing patches, or configurations not complying with security policies. By providing a comprehensive view of the network’s security posture, scanning tools enable IT professionals to take corrective actions more effectively.
Furthermore, network scanning is not a one-time task but a continuous part of network management. Regular scanning helps keep an updated record of network changes and developments. It plays a crucial role in dynamic environments where new devices are frequently added or configurations change, helping maintain continuous security and compliance.
Network scans are also instrumental in network segmentation, ensuring that devices within a specific segment meet the necessary security criteria. This segmentation can limit the spread of potential intrusions and minimize the impact of an attack.
In summary, network scanning is an essential activity that provides a detailed inventory and security assessment of networked devices, enabling organizations to maintain high levels of security and operational integrity in their network infrastructures. This proactive measure is crucial in safeguarding sensitive data and systems from the evolving landscape of cyber threats.
The Role of Network Scanning Tools
Network scanning tools automate the scanning process to provide real-time insights into network health and security. These tools play a crucial role in preventing data breaches and maintaining network integrity by identifying potential vulnerabilities and irregular activities. By streamlining the detection of security risks, these tools enable faster response times and more efficient management of network resources.
Beyond basic security measures, network scanning tools also facilitate comprehensive network audits. They help organizations comply with regulatory requirements by providing detailed reports and logs of network activity. This aspect is particularly crucial in industries that handle sensitive information, where compliance with standards such as HIPAA, PCI-DSS, and GDPR is mandatory.
Additionally, network scanning tools enhance visibility across the network. They map out the network structure, revealing how devices are interconnected and how data flows between them. This visibility is vital for troubleshooting issues and optimizing network performance. It allows IT teams to pinpoint bottlenecks or failures in the network infrastructure and to understand the impact of network changes before they are implemented.
The role of these tools extends into risk management. By continuously monitoring the network for abnormal activities, such as unusual data transmissions or changes in network configurations, network scanning tools help identify potential security incidents before they escalate into full-blown crises. They also provide the necessary forensic data that can be crucial in investigating and mitigating cyber-attack effects.
Moreover, network scanning tools increasingly incorporate machine learning and artificial intelligence to predict and prevent future vulnerabilities. These advanced capabilities enable the tools to learn from past incidents and to adapt their scanning strategies to evolving threat landscapes, thus providing a proactive approach to network security.
In conclusion, network scanning tools are indispensable in the digital age. They provide critical capabilities for security, compliance, troubleshooting, and optimization within network environments. They protect against current threats and adapt to new challenges, ensuring that networks are resilient and can support the ongoing demands of modern business operations.
Top Network Scanning Tools for 2024
Comprehensive Review of Leading Solutions
- Nmap (Network Mapper)
- Key Features:
- Versatile port scanning capabilities
- Host discovery and service detection
- Operating system identification
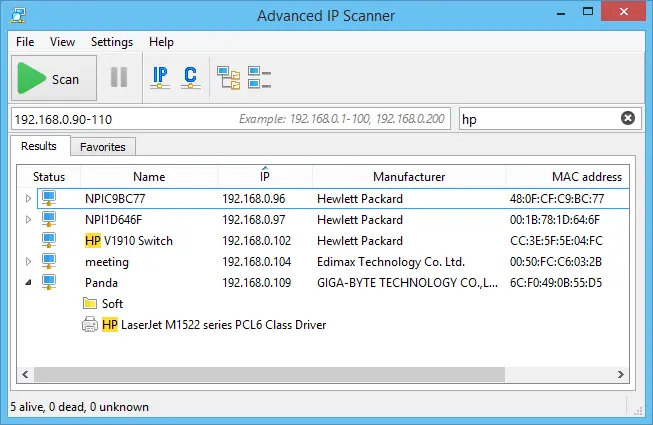
- Advanced IP Scanner
- Key Features:
- Fast and reliable network scanning
- Remote control of devices via RDP and Radmin
- No installation required
- Angry IP Scanner
- Key Features:
- Multi-platform support (Windows, Mac, Linux)
- Export scan results in various formats
- Lightweight and open-source
- OpenVAS
- Key Features:
- Extensive testing for vulnerabilities
- Integrated with Greenbone Vulnerability Manager
- Supports a wide range of network protocols
- SolarWinds Network Performance Monitor
- Key Features:
- Advanced network monitoring
- Automatic network device discovery
- Customizable performance dashboards
Enhancing Network Security with Scanning Tools
Benefits of Regular Network Scanning
- Proactive Vulnerability Management: Businesses can detect and address vulnerabilities by routinely scanning networks before they are exploited.
- Improved Network Performance: Network scanning tools help optimize network infrastructures’ performance and reliability.
- Compliance and Auditing: These tools assist in complying with regulatory requirements by providing detailed logs and reports.
Choosing the Right Network Scanning Tool
When selecting a network scanning tool, consider factors such as compatibility with existing systems, range of features, ease of use, and cost-effectiveness. Tools like Auvik and ManageEngine OpUtils offer cloud-based solutions that provide extensive visibility and management capabilities, making them suitable for diverse network environments.
(FAQs) What are the most effective network scanning tools available today?
FAQs: What are the most effective network scanning tools available today?
1. What are network scanning tools, and why are they important?
- Network scanning tools are software applications designed to identify and analyze network devices, services, and vulnerabilities.
- They are essential for network administrators and cybersecurity professionals to assess their network’s security posture, detect potential threats, and ensure compliance with security policies.
2. What factors should I consider when choosing a network scanning tool?
- Scanning Capabilities: Look for tools that offer comprehensive scanning techniques, including port scanning, vulnerability scanning, and discovery of network assets.
- Accuracy and Reliability: Choose tools known for their accuracy in detecting devices and vulnerabilities without generating false positives.
- Ease of Use: Consider the user interface and ease of configuration to ensure efficient deployment and management.
- Reporting and Analysis: Evaluate the tool’s reporting capabilities, including customizable reports and actionable insights for remediation.
- Compatibility: Ensure the tool is compatible with your network infrastructure and supports the types of devices and protocols used in your environment.
3. Which network scanning tools are highly regarded in the cybersecurity community?
- Nmap (Network Mapper) is widely recognized as a powerful open-source tool for network discovery and security auditing. It offers a wide range of scanning techniques.
- Wireshark is a popular network protocol analyzer that captures and analyzes network traffic in real time, providing insights into network behaviour and potential security threats.
- OpenVAS (Open Vulnerability Assessment System) is a free and open-source vulnerability scanner that helps identify security vulnerabilities in networks and web applications.
- Nessus: A widely used vulnerability assessment tool that provides in-depth scanning capabilities and extensive vulnerability database updates.
- Acunetix: Known for its web vulnerability scanner that detects and prioritizes security vulnerabilities in web applications and APIs.
4. Are network scanning tools suitable for small and large businesses?
- Yes, many network scanning tools offer scalable solutions suitable for organizations of various sizes.
- Some tools offer free or community editions with basic scanning capabilities. In contrast, others provide enterprise-grade features and support for complex network environments.
5. Can network scanning tools be used for compliance and regulatory requirements?
- Network scanning tools play a crucial role in meeting compliance requirements such as PCI DSS, HIPAA, and GDPR.
- They help organizations identify vulnerabilities and security weaknesses that may violate regulatory standards, allowing them to take proactive measures to address compliance gaps.
6. How frequently should network scans be performed using these tools?
- The frequency of network scans depends on factors such as the network’s size and complexity, the level of risk tolerance, and regulatory requirements.
- Regular scans, from weekly to quarterly, are recommended to ensure timely detection and mitigation of security vulnerabilities.
7. Can network scanning tools be integrated with other cybersecurity solutions?
- Many network scanning tools offer integration capabilities with other cybersecurity solutions, such as SIEM (Security Information and Event Management) systems, endpoint protection platforms, and threat intelligence feeds.
- Integration enables centralized monitoring, correlation of security events, and automated response to security incidents.
8. Are there network scanning tools that offer real-time monitoring and alerts?
- Some advanced network scanning tools provide real-time monitoring capabilities and alerts for suspicious activities, unauthorized access attempts, and security breaches.
- Real-time alerts enable organizations to respond promptly to security incidents and minimize the impact on their networks.
Conclusion:
Network scanning tools are indispensable for modern cybersecurity strategies. With the digital sphere evolving rapidly, these tools provide the necessary foresight and protection against potential cyber threats, ensuring that networks are resilient and compliant with global security standards. Whether you are part of a small firm or a large enterprise, integrating advanced network scanning tools into your security framework in 2024 will be a pivotal step toward achieving robust digital health and operational continuity.
This blog post provides a comprehensive overview of network scanning tools, highlighting their importance and detailing the top solutions available in 2024. By staying informed and proactive, businesses can safeguard their networks and ensure their digital assets remain protected in an increasingly interconnected world.